Dr. Web: in October the number of dangerous programs grew by 197%Anna Saveleva | 06.11.2020


Almost a threefold increase caused by the spread of applications protected specialized utility Tool.Obfuscapk.1, through which the code loses a readable form, but retains its functionality
which complicates detection.
In October Dr. Web for Android detected on the protected Android devices at 12.36% more threats than the previous month. According to the statistics of detektirovanie, the number of malicious
programs increased by 9.08%, undesirable by 6% and potentially dangerous on 197.24%. The number of detected adware applications at the same time decreased to 1.51%.
On Google Play there are many new Trojans of the family Android.FakeApp, which was spread under the form of programs, reference books, ostensibly to help in getting tax deductions and
social compensation. In fact, they have uploaded the fraudulent web sites through which users have removed sensitive data and money. Another discovered Trojan is
Android.HiddenAds.2314 intended for showing Intrusive ads and spreads in the guise of a graphic editor.
The “stars” category
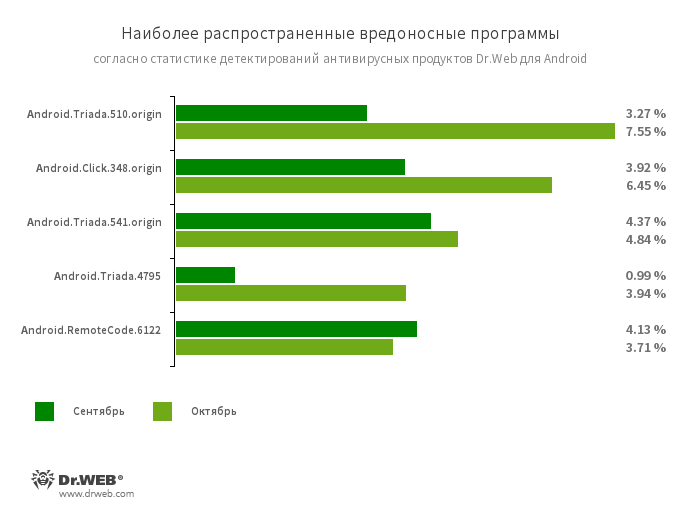
Android.Triada.510.origin .541.origin and .4795 is a multifunctional Trojans that penetrate into the processes of all running programs. The family can be introduced to IOS and Android devices more
at the production stage. In addition, some modifications can exploit the vulnerabilities to gain access to protected system files and directories.
The App Android.Click.348.origin independently downloads the websites, clicks on banner ads, and clicks on links. May spread under the guise of a harmless software. At the same
time FOR Android.RemoteCode.6122that downloads and executes arbitrary code, depending on the modification can control the same functions.
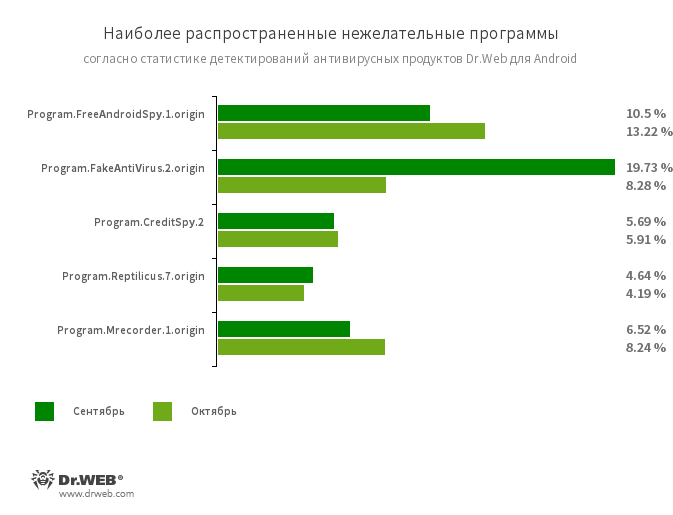
Program.FreeAndroidSpy.1.origin .7.origin and .1.origin are applications that monitor the owners of Android-devices and is able to control the location of gadgets, to collect information about the
SMS-correspondence, conversations in social networks, to copy documents, pictures and videos to listen to phone calls and surroundings, etc.
The most harmless Program.FakeAntiVirus.2.origin mimics the anti-virus software can report non-existent threats and to introduce users to the confusion, requiring you to pay for the purchase
full version.
Program.CreditSpy.2 uploads to a remote server via SMS messages, contact information from the phonebook, call history, and other information.
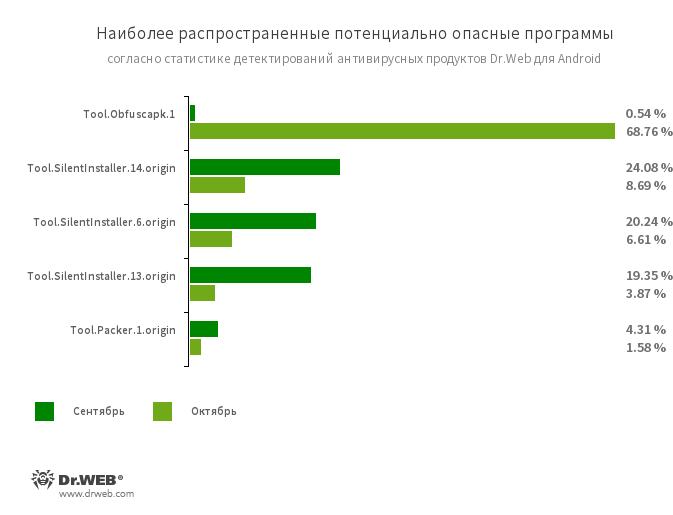
Utility Tool.Obfuscapk.1 is used for automatic modifications and obfuscation of the source code of an Android application to complicate reverse engineering, that helps with detection
antivirus. In turn, the Tool.Packer.1.origin is not malicious, however, has similar functionality and can also be used for Trojans.
Tool.SilentInstaller.6.origin .13.origin and .14.origin is a software platform that enable applications to run apk files without installing them. They create a virtual environment
of performance, which does not affect the underlying operating system.
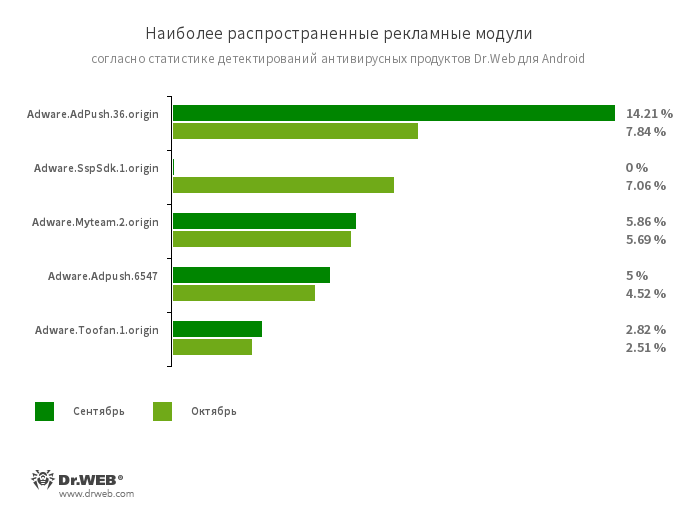
Adware.Adpush.36.origin and . 6547, Adware.SspSdk.1.origin .Myteam.2.origin .Toofan.1.origin is a software module embedded in an Android app and is intended for display
Intrusive advertising on mobile devices. Depending on the family and the modifications they can show ads in full screen mode, locking the Windows of other applications, display various
notice, create shortcuts and download websites.
Threats in Google Play
Of the 17 new versions of the family Android.FakeApp, some got Android.FakeApp.208, Android.FakeApp.209, Android.FakeApp.210, Android.FakeApp.212, Android.FakeApp.213,
Android.FakeApp.214, Android.FakeApp.215 and Android.FakeApp.216. Room 211 got a fake program sports. In total, these Trojans are downloaded over 105 000 owners
Android-devices.
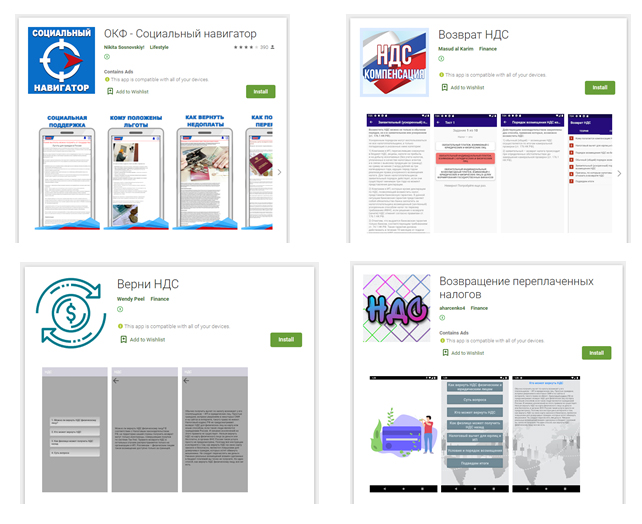
When they start offering the victim to provide personal information, ostensibly to check the available monetary compensation. After payment is “found”, the user is prompted for
for more information, and then he offered to pay the tax or fee for the translation of the “return” of money that gives access credit card details.
Family Android.HiddenAds this month pleased with the Trojan Android.HiddenAds.2314, which when executed hides its icon from the list ON the menu of the main screen, and then starts to show
advertising on top of all other applications and operating system interface.
cybersecurity
Doctor Web | Dr. Web








