The use of Open-Source technologies and components in the enterprise is growing all the time. Thus, security risks, so at least the result of the Vera code submitted to the study, “State of Software Security potentiate but”.
97 percent of all Java applications contain unsafe components. This was the result of the security vendor Veracode in the study, “State of Software Security“. As in the case of Open-Source programs, certain components are re-used, to result in high systemic risks. In an analysis of the provider can show that a single popular component with a critical vulnerability on more than 80,000 other Software components affected. These come in the development of millions of other Software programs.
In the case of Java applications, the result is that around 97 percent of all Java applications contain at least one component with a known vulnerability. This is certainly an extreme example, illustrates how quickly a security vulnerability across the entire software landscape can spread. The data collected Vera code in the past 18 months, over 300,000 automated Assesments.
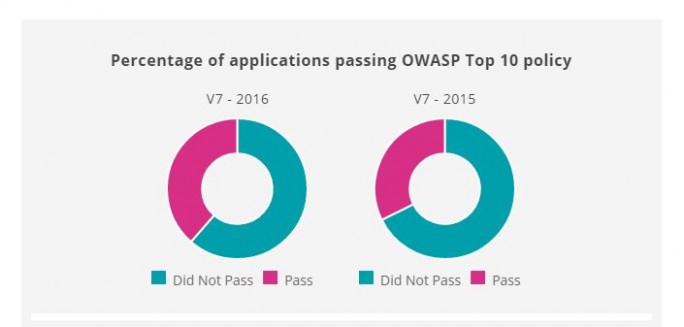
Only a small part of all applications, complies with security standards such as OWASP. (Image: Vera Code)
The same study showed, however, that business users are increasingly aware of the threat. Especially due to the Integration of DevOps and DevSecOps risks at the application level to reduce. And more and more companies use these methods to minimize in the development of applications of security risks.
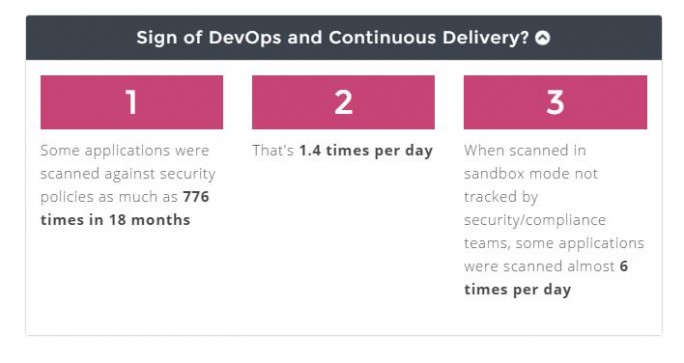 Some of the users are in the App-security-particularly pinngelig and that pays off in an optimized security. (Image: Vera Code)
Some of the users are in the App-security-particularly pinngelig and that pays off in an optimized security. (Image: Vera Code)
“The widespread use of Open Source components in Software development is responsible for uncontrollable systemic risks in companies and industries,” said Julian Totzek-Hallhuber, Solutions Architect at Veracode.
“Today is a cyber criminal can focus on a single vulnerability in a component, to harm millions of applications. All industries and Software are highly application dependent.”
Deserialization Bug for a quarter of the vulnerable applications
A concrete example from the January 2015: at the Time, an Exploit has been widely used Framework for the so-called “Deserialization”programming practice. You can read an object from the hard disk and it is how an application handle. Due to a bug, an attacker could exploit this process for yourself and to arbitrary Code on the compromised System.
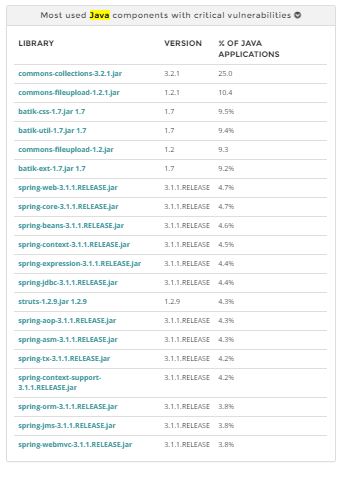 Java components are widely used. These components have a known security leaks, and plug in a variety of applications. (Image: Vera Code)
Java components are widely used. These components have a known security leaks, and plug in a variety of applications. (Image: Vera Code)
In November 2015, the practically exploitable Exploits for JBoss, IBM WebSphere, Jenkins, OpenNMS, and the Oracle WebLogic were known, based all on the error in the Apache Commons Collections. Apache has, of course, closed the leak in the meantime. However, this leak is the most common sicherheheit leak in the analysis of Vera code: The component of the Apache Commons Collections v. 3.2.1 comes after all, in a quarter of all Java applications. In some industries this leakage alone accounted for 67 percent of all the vulnerable Java applications.
Another Detail to 60 percent of the applications already during the first Scan, that basic safety requirements are not met. In contrast, the report shows that companies that use Best Practices and programs with consistent policies and practices for secure development, implement, are in the control of vulnerabilities much more effective than the average. The top quarter of the company, could fix about 70 percent more vulnerabilities than the average.
The provider to submit this study to seven Times. In retrospect, the authors show that the number of vulnerable applications has remained in the past few years, relatively constant. The authors conclude that the large-inform the user in the development of new applications as respects to security. Other loaded in turn, these security policies are only a small part of the portfolio.
Veracode recommends, in addition, Best Practices, such as Remediation, Coaching and E-Learning. As a result, the Fix could Rate by a factor of six to improve. Applications that have been tested with a Developer Sandbox can double the policy-based Fix Rate almost. “Continuous development and implementation of models, as in DevOps environments, can contribute with regular application of the tests for the safe development,” said Nabil Bousselham, Solutions Architect at Veracode.
An analysis of platform data shows that more and more companies are testing applications during the development of the times. With an average App will be tested seven Times. Some applications should be scanned in a period of 18 months, and between 700 and 800 Times.
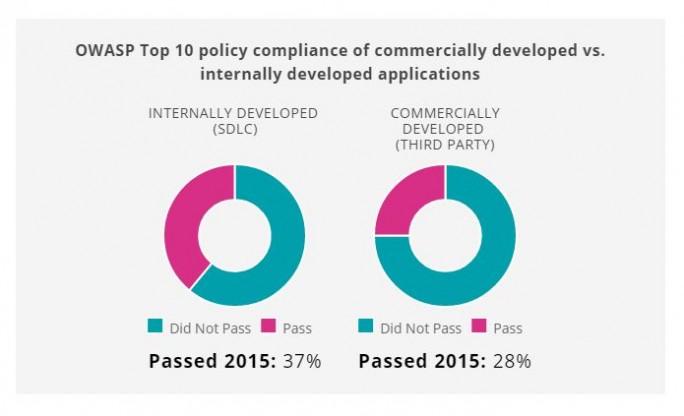 Applications from external developers, correspond to an average of rare safety standards as in-house developed Apps. Companies should demand from the providers, so more care in the development. (Image: Vera Code)
Applications from external developers, correspond to an average of rare safety standards as in-house developed Apps. Companies should demand from the providers, so more care in the development. (Image: Vera Code)
An amazing Detail of the investigation shows that Apps that were developed by the users themselves, comply with common security standards like OWASP or CWE/SANS, than those that have been developed by an external service provider. Also, the authors of the study, but was also already in the past years already.






