No more Git by password GitHub authentication by token
The warnings on GitHub are piling up: From August, Git access will no longer be possible via password. Personal Access tokens are intended to replace your usual authentication.
 Anyone who wants to access Git through GitHub CLI or APIs will need to switch their authentication to tokens.
Anyone who wants to access Git through GitHub CLI or APIs will need to switch their authentication to tokens.
Anyone who has been working with GitHub from the terminal lately may have noticed: GitHub warns sporadically that Git access via password will soon no longer be possible.
However, some may have simply ignored these warnings like the everyday update notes. After all, the first warnings were issued many months ago. And who cares about annoying changes that will only take effect in a year? From August 13, access by password is no longer possible.
You should also be prepared for the 30th of June: Between 9 and 12 o’clock and between 18 and 21 o’clock access by password will be completely blocked! This planned “brownout” will be repeated on 28 July. If you work with GitHub on a daily basis, you should change the account beforehand to avoid outages.
Security through tokens
GitHub already pointed out the switch to Git authentication in July 2020-and now it’s getting serious. Instead of password authentication, you will have to use tokens in the future. This applies to any Git access via command line or desktop application, as well as any apps and services that access your GitHub repos. Only GitHub Desktop and Enterprise server customers are left out.
The motivation should be clear: GitHub has done a lot for security in recent years, from optional two-factor authentication, to alerts for login attempts, to checking passwords for occurrences in larger data leaks via HaveIBeenPwned. Access via username and password was initially retained purely for compatibility reasons.
While authentication with tokens requires a little effort at first, it has some advantages: Tokens are unique and can be created for individual uses or devices, they can be recalled at any time, are not susceptible to Bruteforce attacks as random strings and can be configured for very specific rights and tasks.
Create Personal Acces Token
So if you use the GitHub API or the command line, you have to change it to a Personal Access Token (PAT) – this works as follows:
First of all, if there is one, you need to get rid of your saved password. As a rule, unless otherwise set, this is simply in the keychain. “git config –list / grep credential” provides a quick overview.
If “store” is found here, Git has stored the password locally and unencrypted. In this case, the cache can be opened with “git config –global –unset credential.helper “(if applicable without a global specification) and the data itself can be found by default under ” $HOME/.git credentials.
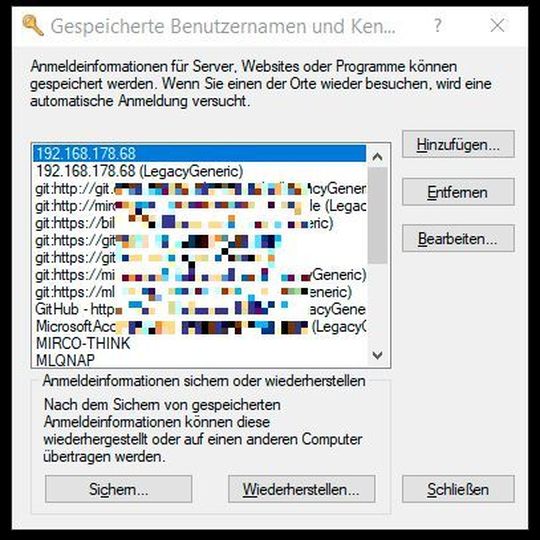 Rare sight: Keychain windows of Windows.
Rare sight: Keychain windows of Windows.
(Picture: Lang / Microsoft)
If the keychain can be found here, the access must be deleted accordingly. Under Linuxen, the handling of this should be self-evident, under Windows, however, not. The Windows own administration is output with “wincred” in the above query. The Windows keychain can be found from the Control Panel under “Control PanelAll Control Panel ItemsCredential Management”.
Something more universal works the command “rundll32.exe keymgr.dll, KRShowKeyMgr ” from the terminal. Typical Windows: The two ways call the same content, but under different surfaces. No matter which window you land in, here you can delete the saved GitHub data.
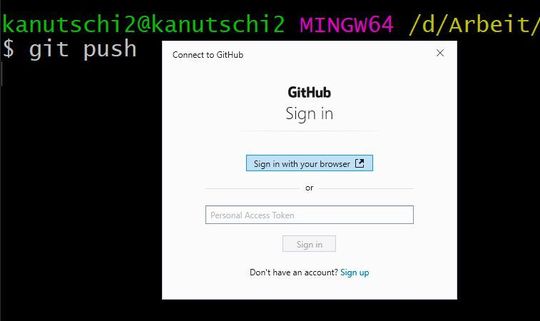 Authentication for Git commands with tokens only.
Authentication for Git commands with tokens only.
(Image: Lang / GitHub)
The next time you try to push through the terminal, the password entry window will appear again. Now you can create a PAT in GitHub’s web interface. This function can be found under the “Settings” in the user menu at the top right, not in the “Settings” of the individual repo. So call ” Settings / Developer Settings / Personal access tokens “and create a token via” Generate new token”.
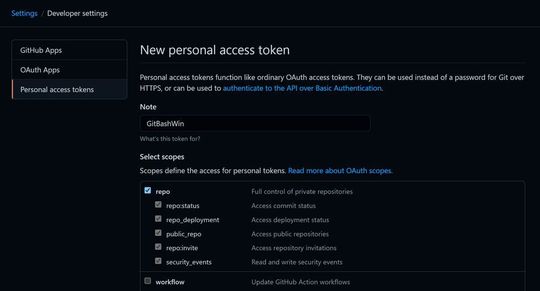 GitHub tokens can be precisely tailored.
GitHub tokens can be precisely tailored.
(Image: Lang / GitHub)
As a result, you get a long list of “scopes”, individual areas for which this token should be authorized. An explanation of the individual areas can be found in the GitHub Docs. For full access via command line, a check mark at the top of “repo”is sufficient.
After saving you get one time (!) to see the token, which you can now use like a normal password and of course should treat accordingly. For the next Git action to be authorized, simply enter the token as a password. Then the git workflow works as before.
Two-factor authentication and SSH
Users who previously used SSH keys to regulate their authentication are not affected-this variant is still possible. Users of two-factor authentication also do not have to do anything else, as this already implies the use of tokens on GitHub.
Consequently, as an alternative to the above procedure, you can also activate 2FA via “Settings/Account security” to secure logins to the GitHub website with a second key, which as usual is delivered by the smartphone via app. The authentication on the command line concerns this only insofar as a token is required-but for a” git push ” you do not have to specify a (second) key every time.
One can certainly admit that GitHub has implemented the whole procedure very user – friendly and unagitated- a year of sporadic warnings, two explicit warning days with planned downtime and proper background information should prevent any problems in August. Nevertheless, the urgent tip: Take action immediately, now the topic is just present!
By the way: Not only the pure Git access to GitHub is affected, API requests and apps also have to be adapted if necessary, so that e.g. from …
curl -u my_user:my_password https://api.github.com/user/repos
… a query like …
curl -H 'Authorization: token my_access_token' https://api.github.com/user/repos
… opens. For more information, see GitHub’s developer blog. If you want to learn more about 2FA: 5 free 2FA systems for retrofitting.
(ID: 47443223)








