The fix for this vulnerability could be complex. The first projects have now announced Patches for the most common leak in Java.
A leak in the Apche-Commons-library malicious Code in Java, can-based applications, such as JBoss, Jenkins, OpenNMS, WebSphere, or WebLogic introduce. This is reported by security researchers from Foxglove Security. The vulnerability is based on an uncertain method, with the help of Java objects deserialized.
The gap was for over nine months, known as Foxglove, explains in a Blog. Because Java bundles applications dependent libraries with each application, instead of using Shared Libraries, is the weak point for some time with high probability exploitable.
“Each application server comes with its own package of libraries. Worse still, any application that is installed on the Server, with often brings their own collection,” writes security researcher Steve Breen. “To fix this completely, you must identify each individual library and update.”
Breen has also developed an Exploit for the vulnerability. It is based according to him, on a similar vulnerability in the Apache Commons in connection with the deserialization of objects was made in January, open to the public.
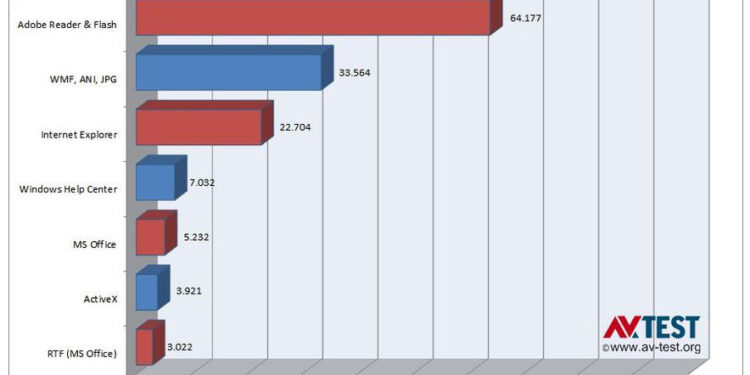
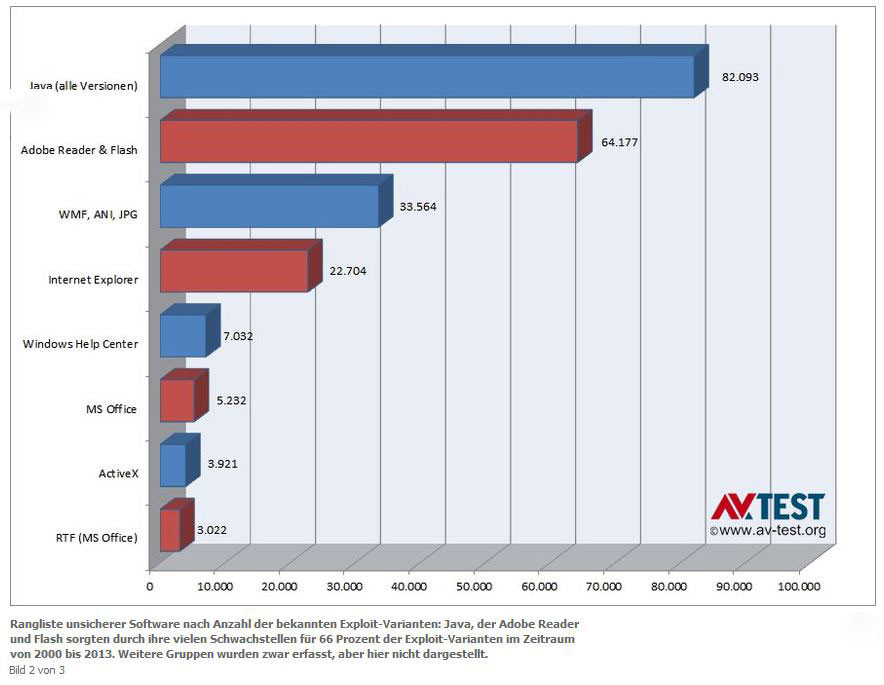 Java, Reader, and Flash to draw for 66 percent of all pests and pest variants in the past 10 years. Source: AV-Test
Java, Reader, and Flash to draw for 66 percent of all pests and pest variants in the past 10 years. Source: AV-Test
When you de-serialize objects using Java, could Breen to create according to its own information adapted Payloads, in order to gain Shell access. It works on a machine where JBoss, Jenkins, OpenNMS, WebLogic, or WebSphere or Java Remote Method Invocation use.
Apache and Jenkins, meanwhile, have responded, and Patches announced, in order to eliminate the vulnerability. Jenkins published a Workaround, disable the attack is utilized in the Jenkins CLI System. A Patch is scheduled to appear next Wednesday. “Unfortunately, we were not informed prior to the publication of the gap, so that we are still working on a Fix,” said the Jenkins Team.
Similar accusations Jeff Gehlbach of OpenNMS, said via Twitter, Breen would have had to inform the affected projects first of all, about the Zero-Day vulnerability, before he made them publicly expressed. Justin Kennedy of Foxglove replied, that it had considered a weak point as a Zero-Day vulnerability.
The Apache Commons is 3.2.x branch to a proposed Patch extends, so that the serialization of the vulnerable Invoker TRANS-shaper class by Flag by default, turn it off. “When using the new Version of the library, any attempt to deserialize an Invoker of the TRANS-former will result in an exception”, like Apache-Commons-developers Thomas Neidhart explained.![]()
[mit Material von Björn Greif, ZDNet.de]
Tip: Do you know the history of computer viruses? Check your Knowledge – with 15 questions on silicon.de